SQL Injection - A Problem old, still present.
Summary:
This article aims to demonstrate that the vulnerability caused by incorrect implementations in the application code, are still in use,
although there are already good practices that, if applied, prevent or mitigate the SQL Injection threat from happening.
Introduction
First of all, what would be the definition of SQL Injection ? As described in
Wikipedia, that would be the classic definition:
SQL Injection is a type of threat of security that takes advantage of failures in interacting systems with databases through
SQL commands, where the attackeris able to insert an improper custom SQL statementinside a query (SQL query) through data entries
from an application, such as forms or an application URL.
There is threat, currently
Recently, a contributor to our DBA Team sent me the link below with the ranking of various vulnerabilities in applications:
The Common Weakness Enumeration (CWE™) is a community dedicated to identifying
software and hardware vulnerabilities, helping their classification and
categorization. In the above work, CWE used the following databases
National Vulnerability Database (NVD) of the National Institute of Standards and
Technology (NIST):
- Common Vulnerabilities and Exposures (CVE®).
- Common Vulnerability Scoring System (CVSS)
The SQL Injection threat, classified with the code CWE-89 appears in the position
number 6. A 23-year-old problem still ranks in the top 10, along with
more recent and modern “vulnerabilities”.
The subject is still explored by the Academy, as can be seen in recent articles:
Preventive measures
When, a few years ago, we received the mission to develop a system in PHP with Oracle, I had the concern to explore this subject. Fortunately, the
Oracle released an ebook, which demonstrated the correct way to program to mitigate SQLi.

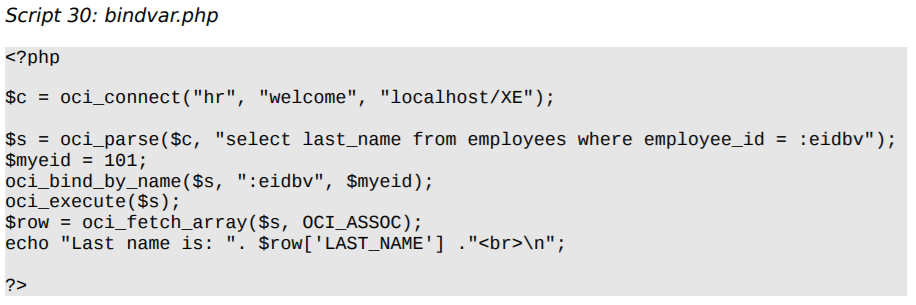
The example above, taken from the book, shows one of the side effects of using the code. more secure. The developer
writes more. Write dynamic SQL with several SQL Injection – An old problem, still present.5Filter options make code denser.
But on the other hand safer.
Some newer languages like Javascript supported by Node.js also offer alternatives to avoid SQLi. Oracle, for example, has developed a add-on for Node.js called node-oracledb that allows the execution of prepared statments with bind variables.
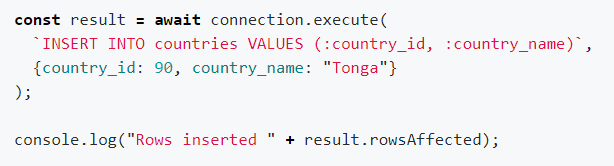
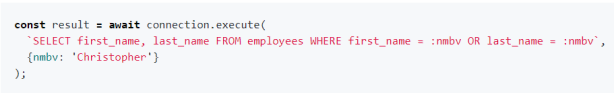
Obviously, the examples above demonstrate the use of lower-level code,
with explicit SQL declaration and direct access to the database.
Actions by the Development Area
- Use “Prepared Statements” instead of SQL with concatenation of variables;
- Handle form input fields, checking data types,
limiting the size of input data, parsing and replacing characters
specials etc; - Use an ORM (Object Relational Mappers) framework such as Hibernate, Entity
Framework, Sequelize, etc… Practically all programming languages
most popular have an ORM framework available;
Actions by the Infrastructure Area
- Monitor the SQL code executed in the database and notify the Area of
Development on suspicious or costly SQLs (task performed by Polo
IT through DBA CENTER!); - Use a WAF (Web Application Firewall). It doesn’t necessarily detect a
SQLi, but when analyzing the URLs that are submitted to the system, it can
identify malicious URLs that could potentially execute an SQLi. - Use Database Firewall. This product, among other features, detects
potential threats with SQLi. There are several suppliers that cater to the
most popular databases. to Polo IT recommends using Oracle Database
Firewall, which in addition to working with Oracle, supports SQL Server, PostgreSQL,
MySQL, DB2 and other products (
https://www.oracle.com/pt/database/technologies/security/audit-vault-firewall.html). - Limit permissions on tables in a system, especially on tables
data dictionary reviews as well as business critical tables. It is
activity is a joint work between the Development Area and the DBA.
Many systems have their application user with DBA privilege,
SYSADMIN or similar. If the hacker is successful in SQLi, the possibility of it
extracting information that might extend your attack radius would be minimized by
if you take this approach. - Encrypt sensitive columns. Many databases, with information from
login and password were captured through SQLi, and the password column was with
the text in its literal form. Obviously, a more technical hacker when realizing that
the data is encrypted, it can search for the key to decrypt, but the
depending on how this technique was implemented, this task will be much more
difficult to implement.
Conclusion
Constantine Jacob Michael
Partner and technology manager at Polo IT
DBA and Database Teacher
Oracle Autonoumous Database Cloud Specialist
Oracle Cloud Infrastructure Architect